c#
WebFileManager updated
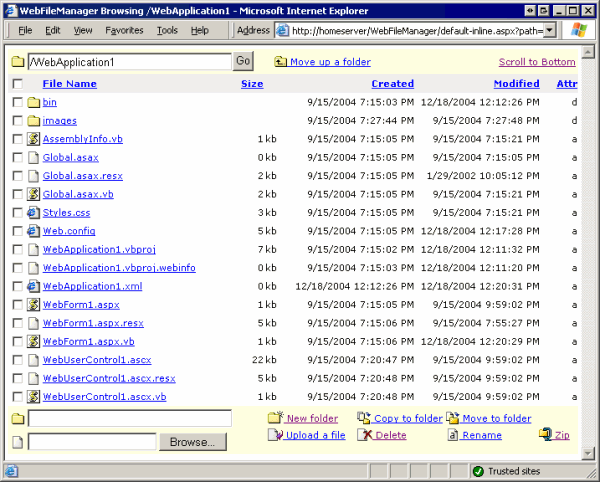
I updated the WebFileManager CodeProject article with some enhancements. It now supports zipping files and column sorting: I included both the code-behind and inline code versions of the page in the solution archive this time. There’s also a new dependency on SharpZipLib, assuming you want the remote file zipping