security
CAPTCHA is Dead, Long Live CAPTCHA!
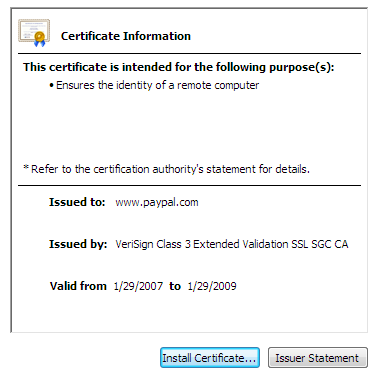
In November 2007 I called these three CAPTCHA implementations “unbreakable”: Google (unbreakable)Hotmail (unbreakable)Yahoo (unbreakable) 2008 is shaping up to be a very bad year indeed for CAPTCHAs: * Jan 17: InformationWeek reports Yahoo CAPTCHA broken * Feb 6: Websense reports Hotmail CAPTCHA broken * Feb 22: Websense reports Google CAPTCHA broken