You may be a victim of software counterfeiting.
Microsoft has finally activated the most aggressive part of their Windows Genuine Advantage program – active notifications.
After downloading the latest Windows updates, if your Windows cd-key doesn’t validate against Microsoft’s online database of cd-keys, you may be greeted with this unpleasant five-second mandatory delay dialog at the login page:
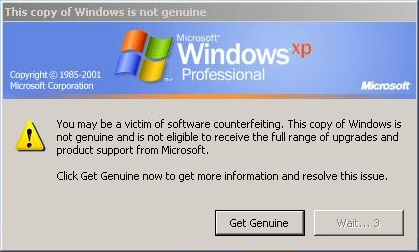
On top of that, you get a repeating balloon notification that nags you periodically while you use the operating system:
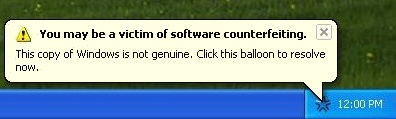
The warnings also get more dire as time progresses:
This copy of Windows is not genuine and you have not resolved the issue. This computer is no longer eligible to receive select security upgrades from Microsoft. To protect your computer, you must click Get Genuine now.
The language here is a little misleading. Microsoft is socially obligated to provide critical security updates to pirated machines. Otherwise those vulnerable machines will eventually be compromised and potentially used in denial of service attacks and other nefarious schemes. Microsoft does provide so-called “critical” updates to all Windows machines, regardless of whether or not they’re genuine.
This is all courtesy of the mandatory “Windows Genuine Advantage Notification” service that is being delivered now through Windows Update. This isn’t just a service you can disable, or a process you can kill in task manager, either. You’ll have to install some kind of questionable third-party hack to get around it.
I suppose it’s only malware if you’re a pirate. What’s a poor, beleaguered user to do? Microsoft offers five options:
- Purchase a valid Windows XP cd-key online from Microsoft.
- If you can produce high-quality counterfeit media, along with a proof of purchase, you can get a free replacement key from Microsoft.
- Contact your reseller for redress.
- Purchase Windows XP from a local OEM reseller.
- Purchase Windows XP at a retail location.
Notice the word “Purchase” appears in three of those five options. There’s almost no way to finagle a free cd-key out of this.
I found a Microsoft presentation on Windows Genuine Advantage (WGA) which goes into a lot more detail. It also provides this graph of WGA validation failure rates across the United States:
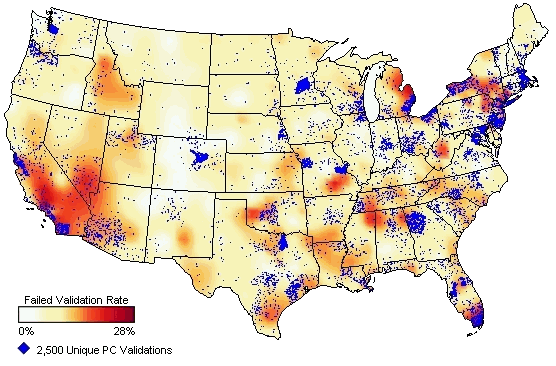
All I can say is, get used to increased forms of online discrimination between genuine and pirated versions of software. Windows Vista will have an even more advanced form of WGA; pirated versions of Vista, for example, will not be able to enable the fancy Aero “glass” interface.
Microsoft is certainly entitled to protect their IP by annoying pirates into buying cd keys. But I wonder if they’re veering too far into the enforcement side of the optimal piracy rate.









