security
Windows Vista: Security Through Endless Warning Dialogs
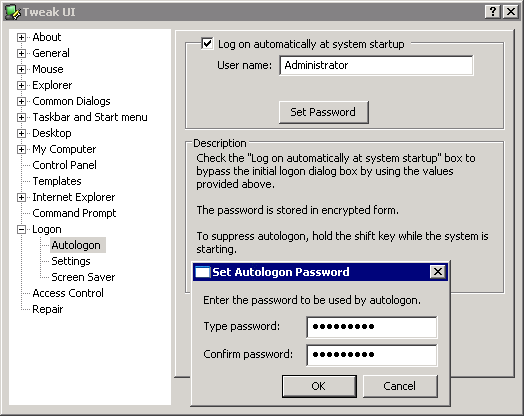
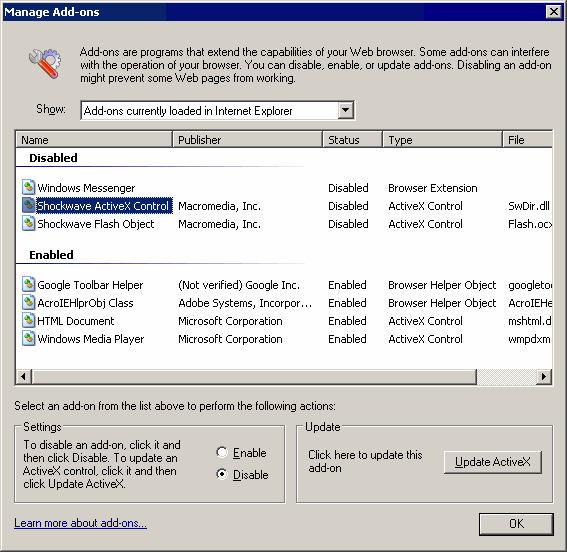
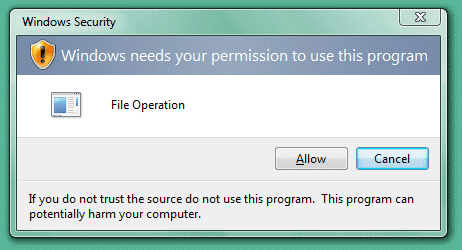
Paul Thurrott’s scathing article Where Vista Fails highlights my biggest concern with Windows Vista: Modern operating systems like Linux and Mac OS X operate under a security model where even administrative users don’t get full access to certain features unless they provide an in-place logon before performing any