security
How to Clean Up a Windows Spyware Infestation
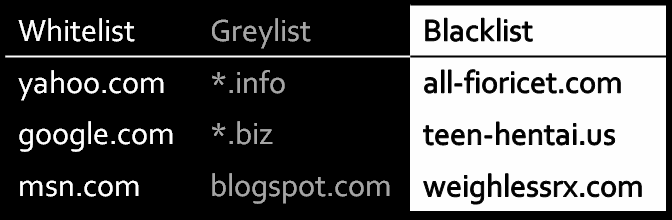
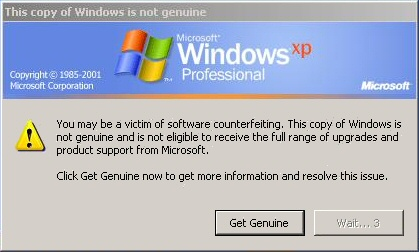
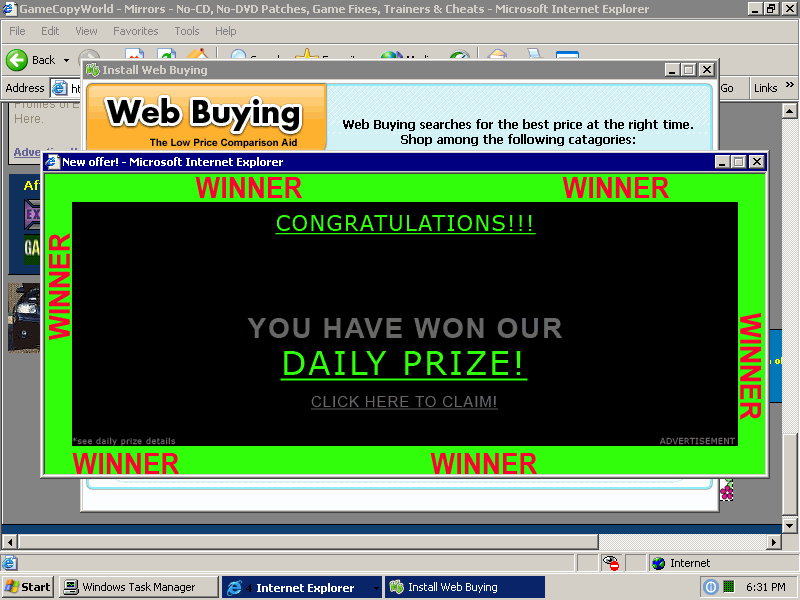
I recently upgraded my dedicated racing simulation PC, so I was forced to re-install Windows XP SP2, along with all the games. As I was downloading the no-cd patches for the various racing sims I own, I was suddenly and inexplicably deluged with popups, icons, and unwanted software installations. I